Windows Architecture Series: Part 3
"You take the blue pill, you wake up in your own bed, and you believe what you want to. You take the red pill, you stay in Wonderland, and I'll show you how deep the rabbit hole goes."
- Morpheus to Neo in The Matrix
[OK, OK, so it's not a spy novel. But it's close.... Funny how that rabbit thing keeps coming up, eh? :-)]
Now that you've been introduced to the Process, let's move on to Virtual Memory. Virtual Memory means that the operating system can allocate more memory (i.e. RAM) than the computer physically has. If your hard drive starts making horrid distracting noises a lot (called "thrashing") then you're probably experiencing an aspect of Virtual Memory called paging (sometimes called swapping). We'll have a whole mini-lecture/rambling on later this week. That is not the only aspect of Virtual Memory, however. Tonight we'll plumb the mysterious depths of the Mythological 4GB Address Space.
Remember the definition of a Process? "Each process has a private virtual address space." This private address space is the Mythological 4GB Address Space.
All right, where does this 4GB come from? Well, we're discussing 32-bit operating systems (for the sake of argument, Windows 95/98/ME are considered 32-bit OSs, even though they contain a fair amount of 16-bit code). If you were to take 232 and lay it end to end, you'd end up with 4GB (4,294,967,296 bits = 4 GB). The 32-bit memory model is flat and linear (as opposed to the segmentation of the 16-bit model).
But what does this all mean? First of all, it's not real. This is all a figment of your imagination. It's an intangible concept. I can't draw you a picture of it or point you to a place where you can see it happening. We have to proceed by analogy alone. So, our analogy is Property - not as in methods and properties, but as in Land. Like folks have in Texas. Texas folks have "Property".
We need a bit of background to start. I'm sure you all have either experienced first hand or heard about the General Protection Fault (GPF) in 16-bit Windows (like 3.1). In a nutshell, a GPF was when one program decided willy-nilly, no permission asked, to take over another program's memory address(es). This would ultimately confuse the processor and chaos ensued. Restarting Windows and clearing out all the memory addresses was the only way to "recover".
Contrast this with another familiar annoyance: "This program has performed an illegal operation and will be shut down" (or a friendly visit from Dr. Watson). The latter does not require a full system restart (OK, sometimes you should anyhow with the Windows 95/98/ME bunch, but that's a whole other story...). Why is this?
The clue is in the formal name of the GPF, specifically the P: Protection. 16-bit memory is not protected. At any given time all programs can see the memory addresses, data, etc. of all other programs. That's why they seem to wait until the worst possible moment (from your point of view - best from theirs...) to decide to play Risk. And, it was designed that way - it's how programs share data in 16-bit land.
32-bit architecture, however, is protected. Any program's process(es) can only see the memory addresses, data, etc. of that particular process. A 32-bit process thinks that only it and the OS are running on the machine. Occasionally a rogue process may attempt to access a memory address that is not its own ("...an illegal operation..."); fortunately the OS discovers this before any damage is done and the process gets shut down. It is very important that you remember the protection aspect.
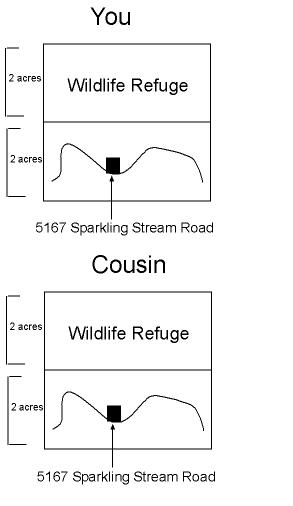
| Now, on to the Property. Let's say you move into town and want to find a place to live. You know a cousin of yours got a really great deal on some land to the West. You end up buying a similar 4 acre ranch outside of town. You're just blissful - all this room for roaming! Well, except for the northern-most 2 acres, the wildlife refuge under the jurisdiction of the County, but other than that area you can build a house wherever you'd like! there's even a picturesque stream running nearby. You decide to build the house on the stream. Since the postal service needs to know where to deliver mail to, you have an address of 5167 Sparkling Stream Road. Life is good. All that space! You can put your cows any where you want! Plant a garden wherever! |
|
Yeah, right.
Just like in The Matrix, you would be laboring under a pretty huge delusion. The reality is that you are actually living in a tiny little apartment next door to dozens of other folks who all think they have 4 acre spreads outside of town. But, since you dutifully take your blue vitamins every morning, you never know about it....
Alrak's Course Resources ©2002-2007 Karla Carter. All rights reserved. This material (including, but not limited to, Mini-lectures and Challenge Labs) may not be reproduced, displayed, modified or distributed without the express prior written permission of the copyright holder. For permission, contact Karla.