ActiveX Security (featuring the Virus ActiveX Control!)
Security is a very big topic these days - as well it should be. You've learned in this course how to implement some basic Internet-enabled applications through using Microsoft's ActiveX technologies such as ActiveX controls and documents. These nifty critters, being full-fledged applications, with access to not only your hard drive, but also your system Registry, can be very scary to network administrators and sophisticated end users. If you let an ActiveX control or document onto your machine you are taking a risk. (Even if the company that created said ActiveX critter is Microsoft. Read carefully the documentation that comes with Service Packs or Updates. Quite a few of those fixes are to plug a hole that some clever hacker found in a Microsoft component.) You need to be aware of these risks and consider that security-sensitive folks may not want to run your ActiveX-based Web site on their machine.
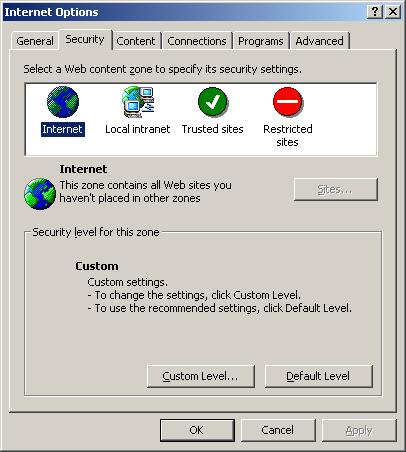
Internet Explorer being Microsoft's browser, it makes sense that it is uniquely designed to take advantage of ActiveX. (Other browsers are not, so if you had broad visions of Netscape and Opera users seeing your site in its full ActiveX glory, you'd best give those up.) One of the neat features of Internet Explorer is how it wants to help the user with security. If you bring up the Internet control panel (Tools->Internet Options) and go to the Security tab you'll see that IE uses the concept of zones.*
You can tell which zone you are in by looking at the bottom right hand corner of your browser window. It will most likely say "Internet", but possibly one of the other zones instead. Every so often you will see it say "My Computer" which means you are viewing Web-enabled content from a hard drive (or removable media).
The interesting thing about the browser window showing that it is the My Computer zone is that you'll notice there are no settings available for the My Computer zone. So, you cannot modify settings and see what happens if you only run html pages from your computer. You'll need to have access to a Web server, either through Personal Web Server or some space on Geocities or FortuneCity or your ISP-provided nominal space. (The Web server does not have to be a Microsoft Web server - we are talking what happens on the client only and as long as you test with Internet Explorer it doesn't matter if you test what is stored on a Linux or Macintosh server.) This is very important to remember later on.
OK, so what is the meaning of these zones and what sorts of settings are there? Let's bring up the Custom Level settings under the Internet zone.
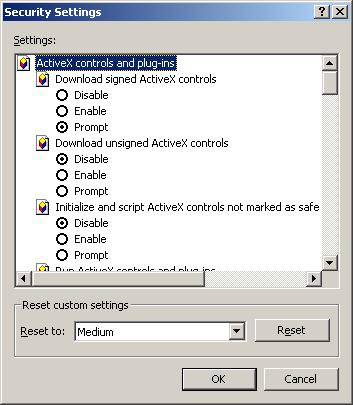
The first three settings refer to ActiveX controls. The first two references to "signed" versus "unsigned" have to do with whether or not the author of the control has acquired a digital certificate from a certificate authority (CA) such as VeriSign. This signing falls under the technology known as Authenticode. It is not a promise that the control works or is not going to wreak havoc on your machine. It merely states that, yes, the CA knows who signed the control and the control is as it was when signed (no tampering has occurred between signing and downloading). The CA cannot hunt down and prosecute someone whose control erases your hard drive. The CA is limited to yanking the digital certificate of said bad programmer if you were to protest to them. It's essentially an honor system. It has no teeth and no intrinsic protection for your system.
The third setting is perhaps the silliest one on the whole list. Let's look at how an ActiveX control is marked as safe or not safe:
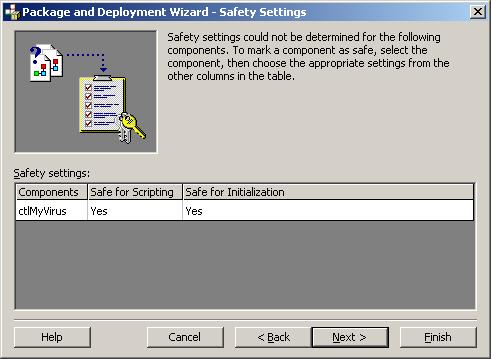
Hey! It's our friend, the Visual Basic Package and Deployment Wizard! It's going through an Internet Package setup. Now, I ask you, what self-respecting evil-doer programmer would say "no" to these questions? That would certainly merit a mention in "News of The Weird"'s Least Competent Criminals section. If someone is ID-ten-T enough to say "no" I'm certainly not going to enable or even prompt their control.
A little further down on the settings list we find questions about running ActiveX controls and Scripting ActiveX controls.
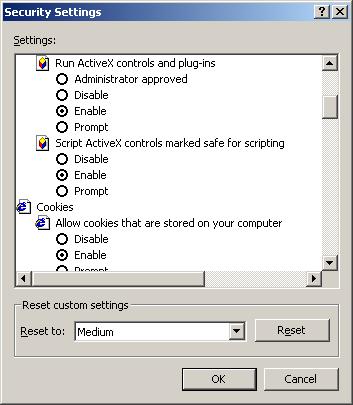
These are backup for the silly setting. Initialize=Run and obvious script=script. Some very security-conscious admins will put disable for these, as well as for the top three, effectively stopping all ActiveX activity (which includes those lovely Flash animations...). Your hope at this point is that if you can prove to whomever that your controls are kind and gentle and worthy they might add your site to the Trusted Sites zone list where security is usually eased up a bit. If you are dealing with an intranet, you can provide URLs that reference internal servers instead of using IP addresses or domain names. There is, of course, a bug ("feature"?) that goes with the Local Intranet zone. The way your system decides that an address is Local Intranet instead of Internet is to look for dots. If it doesn't see dots then it's Local Intranet. The bug is that you can take an IP address (i.e. 202.34.56.100) and turn it into a single block of numbers - no dots. That would mean a mischievous external Internet address would be read into the Local Intranet zone (which often has lowered security as well) and whammo! Red Alert! Red Alert!
There's one more set of security options that involve ActiveX controls, albeit tangentially. These are the Active Scripting.
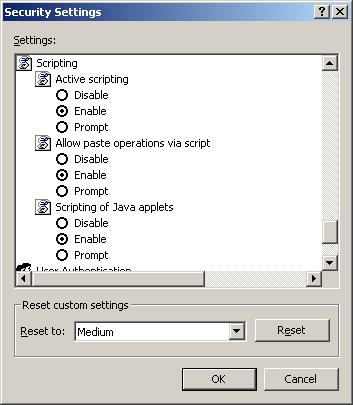
Many controls have some sort of VBScript or JavaScript making them interesting things, especially in a DHTML situation. Active Scripting is not just for ActiveX controls, though. Disabling it will disable all scripting. If you want to test this feature remember what I said above about the My Computer Zone. If you want to see what happens on a page with disabled scripting you'll have to test from a Web server. (If you're really curious you can check out my stuffed elasmobranchs at http://www.bobandray.net - try it with Active Scripting turned off and then again with it turned back on.)
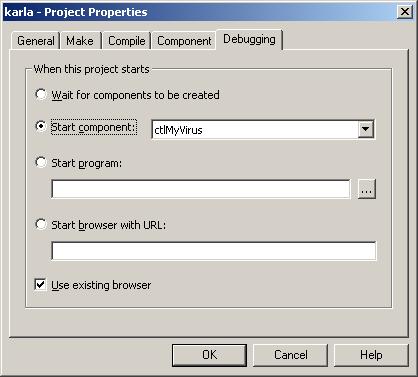
All right, so why do we even care?? Well, let's look at a nice little cute ActiveX control I wrote that I named after myself. I've attached the source code to this post. Go ahead and bring up the Project properties and switch to the Debugging tab. You want the settings to look like this, so that the ActiveX control will display in a browser.
When you run the control you'll get a Web page, with a friendly little message:
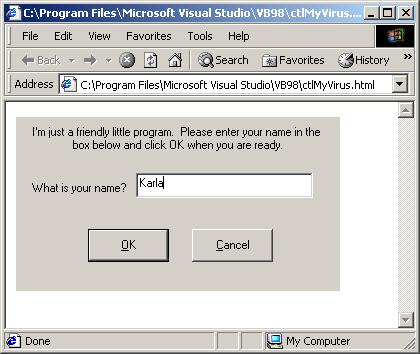
Go ahead and type in your name and click OK. You get this friendly little message box:

What a nice cute little ActiveX control! Now, keep everything open and running and go look at your C drive:
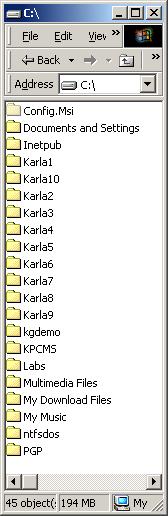
Uh oh...:-(
You can get rid of them - just make sure your name is still typed into the text box and then click the Cancel button. You'll get another friendly message:
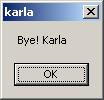
You have just experienced the FileSystemObject - a virus waiting to happen. Here's the code, by the way:
|
At this point you're probably thinking, wow, this ActiveX stuff can get pretty scary. "But, wait!" you cry gleefully, "Java! I can use Java! It's safe! It has this sandbox thingee..." Well, yes, it does. The Sandbox is the Java Virtual Machine and code cannot escape it and run around interacting with system libraries like the FileSystemObject. That is if you don't use Microsoft's Java (whatever that's being called these days...). Microsoft's Java has little hooks into the Windows API and can do all the fun things an ActiveX control can do. It can leave the Sandbox, in other words. And you think you can just protect yourself from it? Lookie!
First we bring up the Java Custom settings.
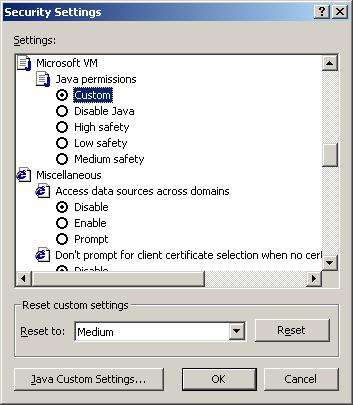
Next we look at the Edit Permissions tab.
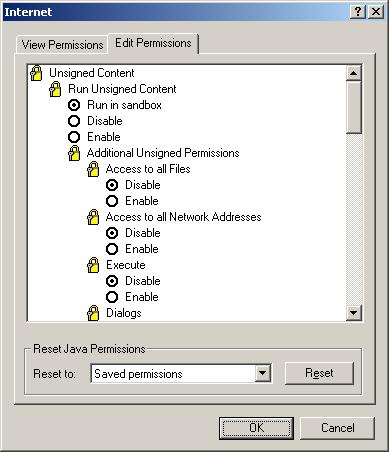
There is a mention of the Sandbox under the Unsigned (yes, that Authenticode can be used for Java Applets, too...) content. That's nice that we can run Unsigned content in the Sandbox where it won't hurt anything. But what about the Signed content???
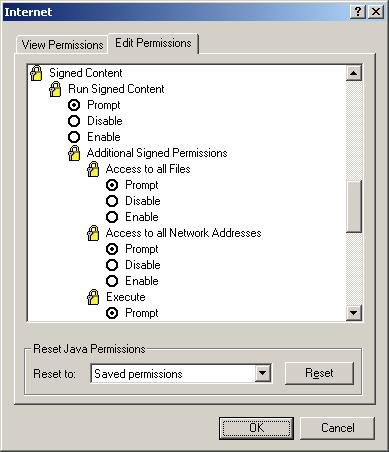
There's no "Run in Sandbox" option for Signed Java Applets. That's disturbing. So, evil-doer programmers listen up! You can use Microsoft programming tools to create evil Java Applets and as long as you sign them there's nothing short of disabling them to contain them! Mwahahahahahaha! Send those tentacles into the Win32 API! Let your bad code run free in the system! Wipe out the hard drive! Ruin the Registry! Hah hah!
[Sorry about that...a bit too much iced coffee...I'll try to calm down now...]
Anyhow, that's my standard security spiel. Knowing how to mark a control as safe for scripting and initializing is handy to know for the test; the rest (hey, that rhymed...) is more of a cautionary tale and useful to the real world as opposed to the test world.
*I personally use the Restricted Zone for sites that have JavaScript-based pop-up ads. I modified the default Restricted Zone settings so that Active Scripting is disabled (if you're saying "huh?" you'll need to read a bit further to get to the Active Scripting section). I've found this feature quite handy, especially on sites that don't have any of their own native JavaScript as it does not diminish and instead greatly enhances the surfing experience on those particular sites.
Alrak's Course Resources ©2002-2007 Karla Carter. All rights reserved. This material (including, but not limited to, Mini-lectures and Challenge Labs) may not be reproduced, displayed, modified or distributed without the express prior written permission of the copyright holder. For permission, contact Karla.